
Welcome To
DAV IT TEAM
We are the solution provider for any type of problems (or) challenges, established in 2019 at (DAV) Head office Gopalapuram Chennai.


A hardware maintenance service typically involves the upkeep, repair, and optimization of physical components within a computing system or network infrastructure.

desktop service involves providing comprehensive support and management for desktop computers within an organization. desktop service aims to ensure the reliability, security, and efficiency of desktop computing environments, allowing organizations to maximize the productivity of their workforce while minimizing downtime and IT-related disruptions.
Read More
"Laptop service" refers to the range of maintenance, repair, and support activities provided for laptops or notebook computers. These services can encompass both hardware and software issues, as well as preventive measures to ensure the optimal performance and longevity of the laptop. Overall, laptop service encompasses a range of activities aimed at ensuring the reliable performance, functionality, and longevity of laptops, addressing both hardware and software issues, and providing support to users when needed.
Read More
Server maintenance involves the ongoing upkeep, monitoring, and optimization of servers within an organization's IT infrastructure. servers through regular maintenance, organizations can ensure the reliability, security, and performance of their IT infrastructure, minimizing downtime and optimizing resource utilization to support business operations effectively.
Read More
Zoho Creator is a low-code application development platform that allows users to build custom business applications without the need for extensive coding knowledge or experience. It enables users to create web and mobile applications tailored to their specific requirements, helping businesses streamline processes, automate workflows, and improve productivity.
Read More
CCTV (Closed-Circuit Television) installation and maintenance services involve the setup, configuration, monitoring, and upkeep of surveillance camera systems for security and monitoring purposes. CCTV service providers help businesses and organizations deploy effective surveillance solutions to enhance security, deter crime, and monitor activities in various environments.
Read More
Biometric maintenance involves the ongoing upkeep, monitoring, and optimization of biometric authentication systems used for security and access control purposes. organizations can ensure the reliability, security, and performance of their biometric authentication systems, enhancing security posture and user experience across various applications and environments.
Read More
Networking devices are hardware components or equipment used to facilitate communication and data exchange between devices within a computer network. These devices play a crucial role in establishing and maintaining connectivity, enabling data transfer, and managing network traffic efficiently.These are just a few examples of networking devices commonly used in computer networks. Depending on the size, complexity, and requirements of the network, other devices such as network bridges, repeaters, gateways, and network switches may also be used to facilitate efficient communication and data exchange.
Read More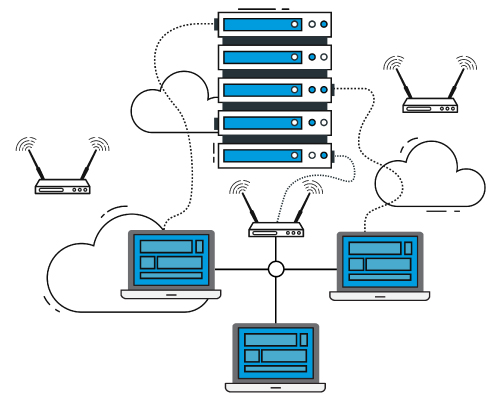
A firewall is a network security device or software application that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Its primary purpose is to establish a barrier between a trusted internal network (such as a company's private network) and untrusted external networks (such as the internet), thereby protecting the internal network from unauthorized access, malicious activities, and cyber threats.
Read More
A Network Attached Storage (NAS) device is a specialized storage appliance or server connected to a network that provides centralized data storage and file sharing capabilities to multiple users and client devices. NAS devices are designed to store and manage large volumes of data, making them ideal for both personal and business use cases.
Read MoreOur team of seasoned IT professionals brings a wealth of expertise and experience to every project, ensuring that we deliver tailored solutions that address our clients' unique challenges and objectives. Whether it's designing and implementing robust IT infrastructure, optimizing business processes through automation, or enhancing cybersecurity posture, we are committed to delivering solutions that empower our clients to achieve their goals with confidence.

Great! As an IT executive, you likely have a wide range of responsibilities that involve overseeing the technological infrastructure and strategies of your organization. This can include managing IT teams, implementing new technologies, ensuring cybersecurity, aligning IT initiatives with business goals, and optimizing IT processes for efficiency and effectiveness.
Read More
An "expert IT team" typically refers to a group of highly skilled professionals with specialized knowledge and experience in various areas of information technology (IT). These teams are responsible for designing, implementing, managing, and supporting IT infrastructure, systems, applications, and services within an organization. Here's a breakdown of the key characteristics and roles within an expert IT team:

Securing information within an organization involves implementing measures and protocols to protect sensitive data from unauthorized access, disclosure, alteration, or destruction. This encompasses a range of practices, technologies, and policies aimed at safeguarding information assets and ensuring the confidentiality, integrity, and availability of data.

A "quick response" refers to a prompt and timely reply or action taken in response to a request, inquiry, or situation. It involves providing a rapid and efficient response within a short timeframe to address the needs or concerns of the individual or organization initiating the communication.

Customer service encompasses the range of activities and interactions provided by a business to address the needs, inquiries, concerns, and feedback of its customers.
IT Head
Executive IT
Executive IT
Executive IT
Executive IT
Executive IT
Executive IT